For all the tech advancements and security improvements that have been made over the past few decades, email phishing continues to be a pervasive threat online.
Because email remains an important tool both personally and professionally, it’s important to understand what email phishing is and how you can protect both yourself and your business today.
We’ll briefly cover what email phishing is, what it looks like, and how you can stay safe online.
What is a phishing email?
Email phishing is a type of online scam that uses a fraudulent email message designed to mimic a legitimate sender. The goal is to trick recipients into disclosing personal information, like usernames, passwords, financial information, etc.
These emails often appear to come from trusted entities, including banks, well-known companies, or even colleagues.
While email phishing isn’t a new type of scam, attackers are now able to use detailed personal information that they’re able to easily gather from social media (or even data breaches) to create highly personalized emails. All of this data makes these emails even more difficult to recognize as a scam.
Not sure of what a phishing email might include? Here’s an older example:
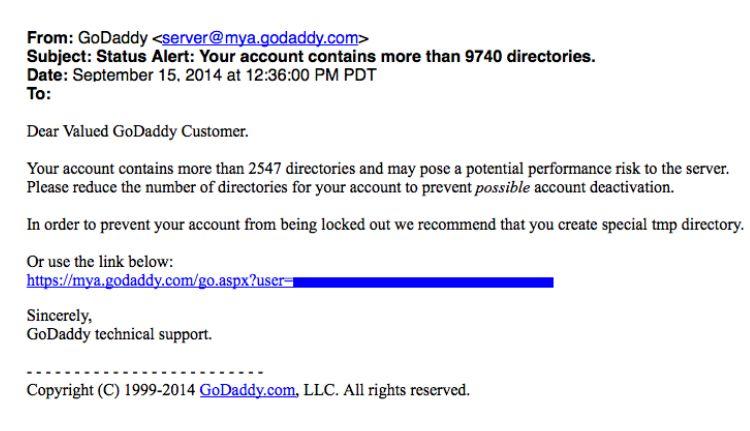
For this particular phishing attack, the goal was to get the recipient to click the account link included. Once a person clicks this link, it directs them to what looks like a GoDaddy login page. However, if you were to hover over the link in that original email, you’d notice it wouldn’t take you to GoDaddy.com, but a fake GoDaddy website instead.
If you clicked the link and attempted to log into the fake GoDaddy.com landing page, your information would be sent to the scammer, and your GoDaddy account would’ve been compromised. Not great.
If you ever receive a phishing email that appears to be from GoDaddy, you can report it to our security team here.
Types of email phishing attacks
There are several different flavors that email phishing can take. Here are a few of the most common email phishing types:
- Email phishing: The most common type of phishing, these emails tend to include links to counterfeit websites or attachments that deliver malware or attempt to capture sensitive information.
- Spear phishing: A more targeted email phishing approach that focuses on specific individuals or organizations. Using data about the person or company, attackers are able to create personalized messages that increase the likelihood of deceiving their victims.
- Whaling: Whaling targets high-profile individuals, such as executives or business leaders. These attacks are focused specifically on stealing privileged information or authorizing fraudulent financial transactions.
- Clone phishing: This attack involves duplicating a legitimate email and altering it to include malicious content. The familiarity of the email layout/format often causes recipients to trust the message without a second thought.
- Spoofing: This technique involves forging the sender's address to make an email appear as if it comes from someone else. Newer DNS requirements have made this type of attack less common, but spoofing can still happen.
Anatomy of a phishing email
Here’s a quick rundown of common red flags in many phishing emails:
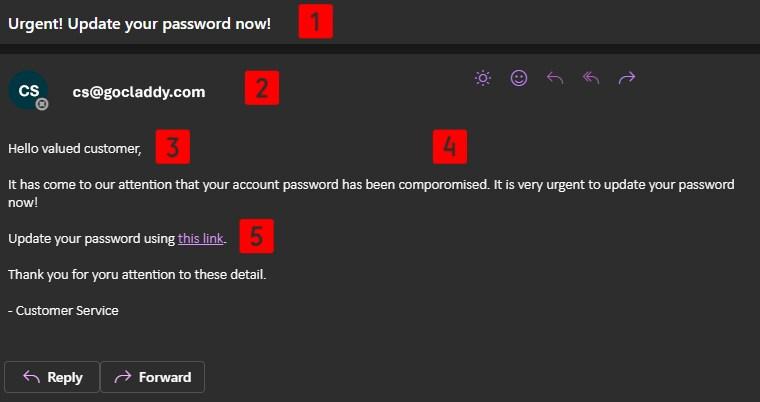
- Urgent/threatening language: The goal is to make you panic and act immediately.
- Suspicious sender address: Carefully review the email address to ensure it’s legit.
- Generic greetings: Another hallmark of a phishing email, scammers tend to be as non-specific as possible.
- Poor spelling or grammar: No one is perfect, but companies tend to carefully spellcheck their email messages.
- Malicious links: Always hover over links and review the pop-up preview before clicking.
What to do if you receive a phishing email
If you receive a phishing email, there are a few steps that you can take to protect yourself:
- Do not click any links or download attachments.
- If the email was sent to your work email address, contact the IT department at your company to let them know. They may ask for a copy of the email for their own records.
- Once you’ve verified that the email message is phishing-related, mark the email as spam (some providers will allow you to report the email message as phishing).
How to protect yourself from phishing attacks
While not all phishing attacks can be fully prevented, you can take these steps to avoid becoming a victim in the future:
- Keep your email applications and computer operating systems fully up-to-date. Security patches are regularly pushed out by software providers, so it’s important to stay current.
- Add two-factor authentication to as many of your accounts as possible.
- If you have employees, make sure to conduct security training regularly to keep them aware of email phishing trends and how to avoid falling for scams.
Staying vigilant is key to staying safe online. And keeping these tips in mind can help you to maintain that vigilance even as email scammers continue to evolve their techniques.







