In this post, we’re going to first learn exactly what a DDoS attack is, how it works, and just how common DDoS attacks really are. Then we’ll cover the easiest and fastest ways to both prevent DDoS attacks, and how to stop a DDoS attack that’s already in progress against your website.
This information will ultimately help you defend yourself against a DDoS attack.
Let’s get started.
Launch your business in minutes with GoDaddy Airo™
First things first: What is a DDoS attack?
The acronym DDoS stands for distributed denial-of-service. DDoS attacks are attempts to make online services unavailable by overwhelming them with traffic. The most common targets for DDoS attacks are large companies, like banks and media outlets. However, it has become more common over the past few years for smaller businesses to find themselves asking how to stop a DDoS attack.
Here are a few interesting facts you might not have known about how common DDoS attacks really are;
- It costs at little as $150 for criminals (or disgruntled customers) to buy a week-long DDOS attack on the black market.
- More than 2,000 DDoS attacks are observed worldwide every single day.
- DDos attacks account for 33-percent of all downtime incidents.
If you’re anything like me, by now you’re probably wondering how exactly these attacks are carried out in the first place. Long before any attack begins, the attackers build networks of infected computers (known as botnets) by spreading malicious software through emails, websites and social media. Once infected, these machines can be controlled remotely, without their owners' knowledge.
They get used like an army to launch an attack against any target.
These botnets can generate huge floods of traffic to overwhelm their target. Traffic gets generated in multiple ways, like sending more connection requests than a server can handle, overwhelming victims with huge amounts of random data to use up the target’s bandwidth. Some attacks are so big they can max out a country's international cable capacity.
It’s extremely important that website developers understand how how to stop a DDoS attack before any major damage is done.
Learn how to stop a DDoS attack in its tracks
If you are currently experiencing a DDoS attack — or believe your web property is going to be targeted — take the following steps immediately for superiort protection:
-
Add GoDaddy Website Security Deluxe.
-
Perform 1-click activation.
-
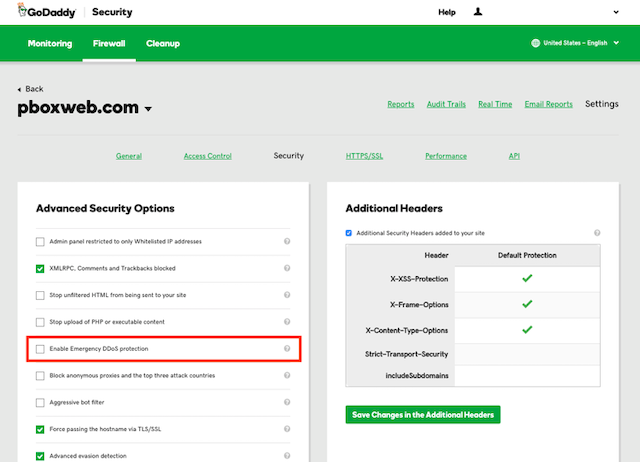
Select “Enable Emergency DDoS Protection”.
-
Block additional countries. (optional)
-
Restrict direct access to server. (optional)
-
Run separate email service. (optional)
Let’s look at each step in more detail.
1. Add GoDaddy Website Security Deluxe
Time: 2 minutes
Difficulty: Easy
GoDaddy offers you an enterprise solution designed to help you mitigate Distributed Denial of Service (DDoS) attacks. The GoDaddy Website Security Deluxe plan will make this technology available to you with a few simple clicks. The service we provide is not dependent on size of attack; it’s a flat fee solution. This plan includes a Content Delivery (CDN), the technology that helps mitigate DDoS attacks, and a Web Application Firewall (WAF), which is the technology that helps mitigate exploitation of vulnerabilities on your site.
We make this process as simple as possible, providing a fully integrated experience.
2. Perform 1-click activation
Time: 2 minutes (or less)
Difficulty: Easy
With GoDaddy’s solution, everything is deeply integrated. All you have to do is click the “activate” button.
This will do all the magic to configure your DNS records.
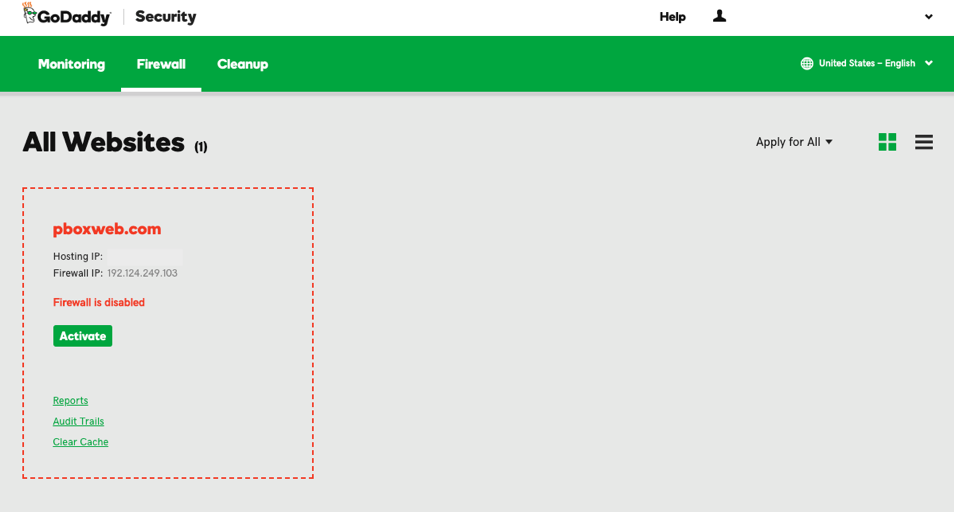
3. Select “Enable Emergency DDoS Protection”
Time: 2 minutes (or less)
Difficulty: Easy
By default, the GoDaddy plans offer you basic DDoS mitigation. When you’re under heavy, unexpected, load you can select the “Enable Emergency DDoS Protection” feature. This will dynamically block all incoming POST requests and you’ll immediately notice a reduced load on your systems resources.
By default, GoDaddy’s plans include both a CDN and WAF.
The above steps will mitigate any external DDoS attacks. There might be additional steps you want to take to harden your environment.
4. Block specific countries and visitors (optional)
Time: 2 minutes (or less)
Difficulty: Medium
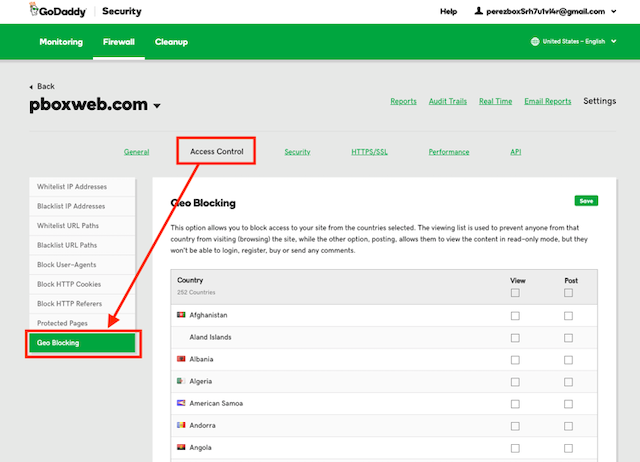
GoDaddy’s Security solution allows you to proactively block entire countries, giving you the option to block either GET (View) or POST (Interact) requests.
If you don’t mind people viewing your content, then blocking all POST requests is what you want. If you don’t want people to see or interact with your site at all, then block both GET and POST requests.
You can perform this action by navigating to Domain Name > Access Control > Geo Blocking.
5. Restrict direct access to server (optional)
Time: 30 minutes (or less)
Difficulty: Moderate
If this is the first time deploying a mitigation tool like GoDaddy’s Deluxe plan, the chances are high that the origin IP of the server has been exposed. This is problematic if the attacker is going directly to your origin IP when performing the attack; in this configuration it’ll bypass any security controls you deploy (like our CDN / WAF).
To help mitigate this issue, you’ll want to block any direct access to the server. You can do this at the web server, or via .htaccess.
You will want to block all direct access, while allowing direct access from GoDaddy’s IP ranges. Those ranges include:
192.88.134.0/23
185.93.228.0/22
2a02:fe80::/29
66.248.200.0/22
Example of what this might look like in .htaccess:
# BEGIN
GoDaddy Firewall Bypass Prevention
<FilesMatch ".*">
Order deny,allow
Deny from all Allow from 192.88.134.0/23
Allow from 185.93.228.0/22
Allow from 2a02:fe80::/29
Allow from 66.248.200.0/22
</FilesMatch>
# END GoDaddy Firewall Bypass Prevention
6. Run separate email service (optional)
Time: 60 minutes
Difficulty: High
If you’re running mail on the same server as your website, the attacker can always find your origin server IP. To close this possible security gap, use an email service on a separate server, whether through your hosting provider or a third-party provider such as O365 or OpenXchange.
Mac users can run this command in Terminal to see which IP is being reported with your MX records:
dig +short $(dig mx +short WEBSITE)
For example, if I was concerned about example.com, I would enter:
dig +short $(dig mx +short example.com)
PC users can run this command in command prompt to see what IP is being reported with your MX records:
nslookup -q=mx WEBSITE
For example, if I was concerned about example.com, I would enter;
nslookup -q=mx example.com
For both Mac and PC, the output will be an IP address that an attacker can always find. Make sure this IP address is different than the one for your web server. If your email is on the same server, no matter how many times you change your web server, the attacker can always find the new IP.
Get proactive
If you’ve ever had to figure out how to stop a DDos attack in progress, you’ll understand the importance of taking a proactive approach to website security. Check out products — like GoDaddy’s Website Security, powered by Sucuri — that offer a Website Application Firewall (WAF) to protect your clients’ sites against DDoS and other threats.
This article includes content originally published on the GoDaddy blog by the following author: Nathan Reimnitz
Meet the 27-hour day.
We built The Hub by GoDaddy Pro to save you time. Lots of time. Our members report saving an average three hours each month for every client website they maintain. Are you adding that kind of time to your day?